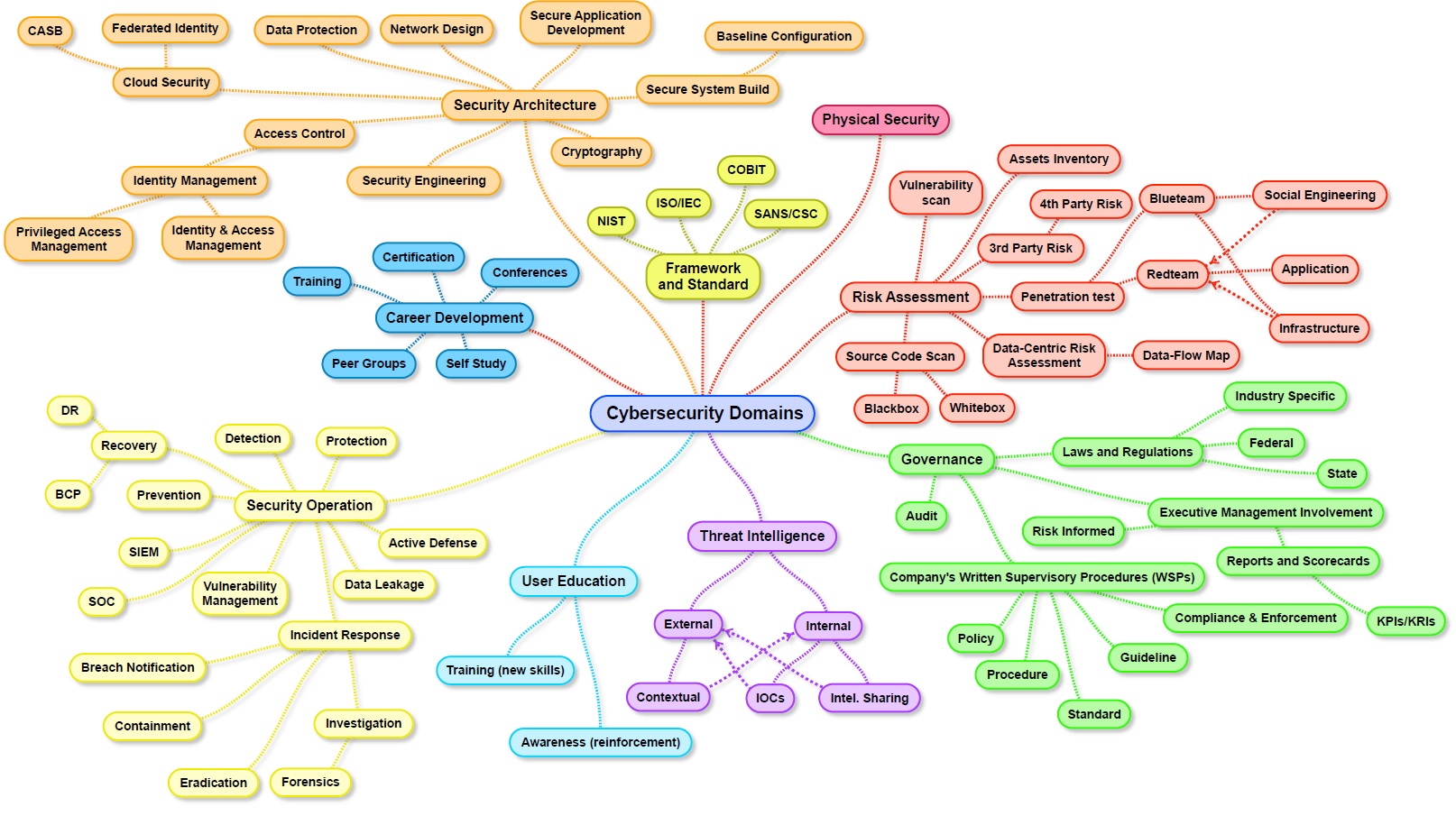
The million dollar question people always ask: how do I get a job in cyber? Unfortunately, the industry is not…
Editor’s note: Women of color were noticeably absent from most of the top women in cyber and top security bloggers lists…
The main difference between a SQL and XSS injection attack is that SQL injection attacks are used to steal information…
We were required to describe at least 2 rules that could be used by Snort to detect an ACK scan,…
We were asked to describe or propose a way to detect ARP spoofing attack and consider possible weaknesses in the…
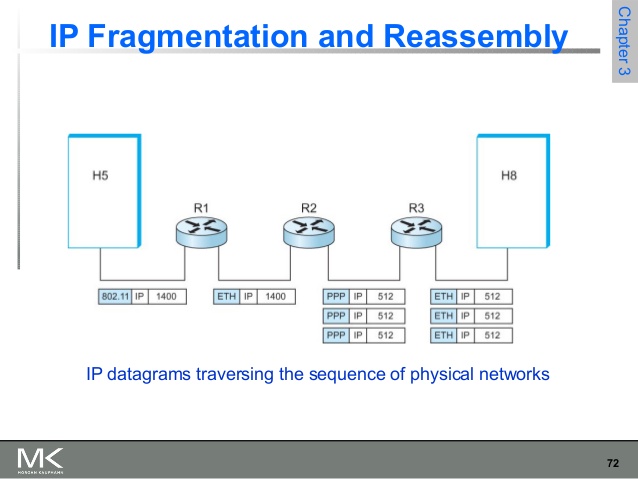
Unlike IP fragmentation (which can be done by intermediate devices), IP reassembly can be done only at the final destination.…
The newly increased focus on cyber security will provide opportunities to make a positive impact, but security professionals should take…
The most damaging corporate computer crime today is hacking large companies that manage our nation’s critical infrastructure, such as electricity…
The most important cyber crime law available to law enforcement is the Computer Fraud and Abuse Act of 1986, commonly…
The American Bar Association requires all prosecutors to make a clear and complete record for review during trial. As with…