We were asked to describe or propose a way to detect ARP spoofing attack and consider possible weaknesses in the…
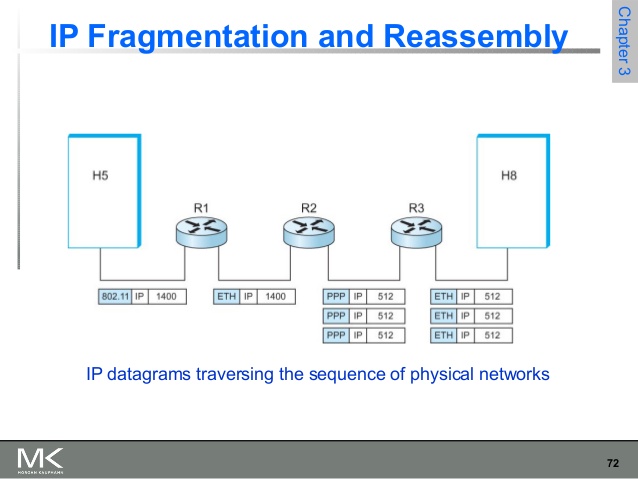
Unlike IP fragmentation (which can be done by intermediate devices), IP reassembly can be done only at the final destination.…
Our weekly course module introduced us to layer 2 attacks, specifically MAC & ARP attacks. I added to the discussion…