I am excited to announce that I am the closing keynote speaker for Diana Initiative Virtual Conference on Saturday 8/22/2020…
Join us on June 20 for Cyberjutsu Con, a virtual event featuring amazing speakers from across the industry. I’ll be…
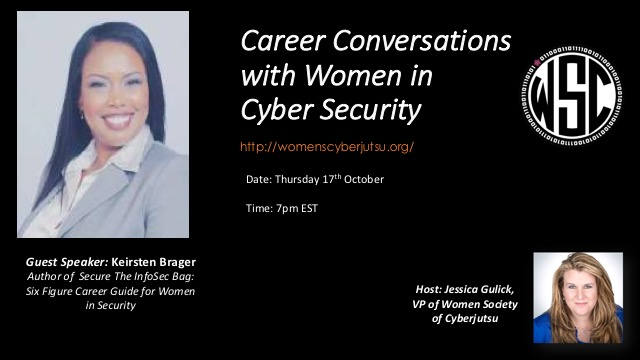
Join us on October 17th at 7pm EST for my career webinar with Women’s Society of Cyberjutsu. We’ll be discussing…
I’ll be speaking at 4pm on the ICS Track: Building a Business Case for Your ICS Security Monitoring Strategy. Abstract:…
I am the Friday morning keynote speaker at Diana Initiative in Vegas this year! I’ll be speaking from 9:50 –…
Join our panel of security leaders on the lunch stage from 11:45 – 1:00 pm at HouSecCon v8. Fresh Perspectives…
One of the ways I try to give back to the community is by using my writing to be the…
You can never go wrong doing the right thing ~ Sam Van Ryder, HOU.SEC.CON Co-Founder and Tripwire Strategic Energy Accounts…